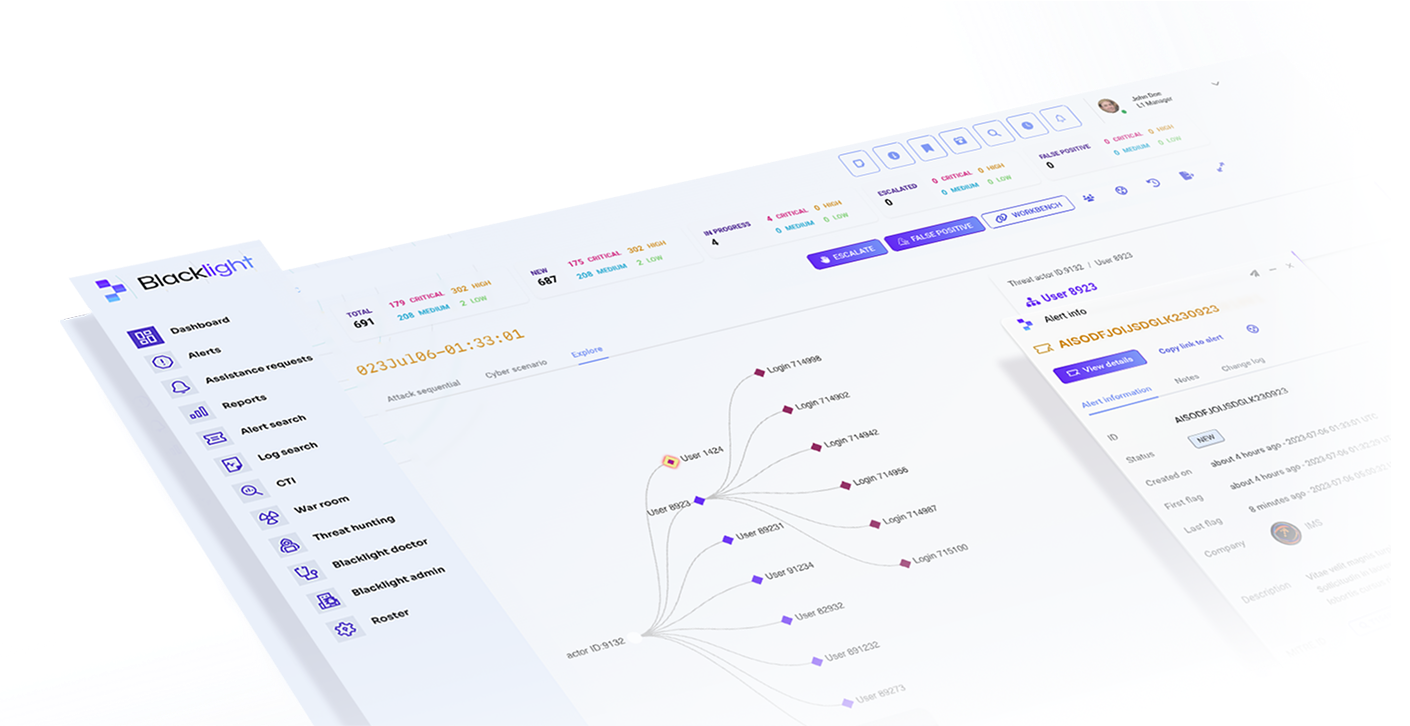
Blacklight Features

Lorem ipsum dolor amet, lociols bolada so
Lorem ipsum dolor sit amet, consectetur adipiscing elit
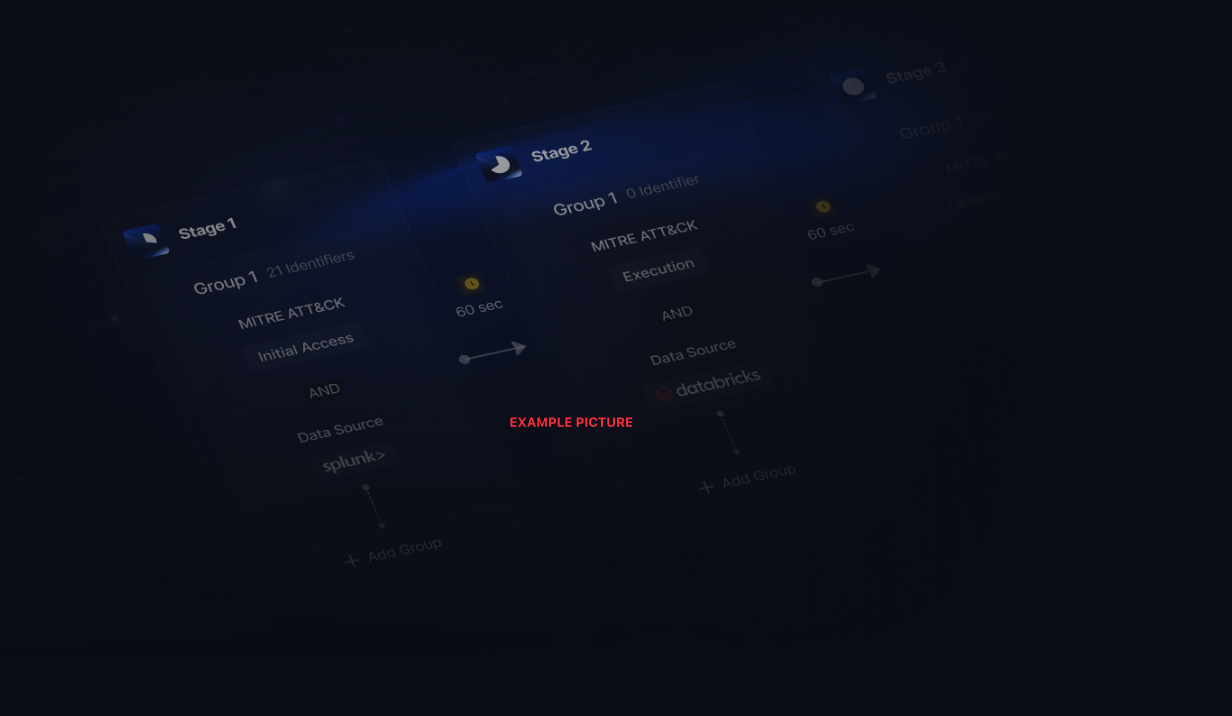
Lorem ipsum dolor sit amet, consectetur adipiscing elit

All capabilities of SIEM-XDR-MDR in one platform
Experience end-to-end visibility, automated response, and complete monitoring for full-stack visibility across hybrid and multi-cloud environments for SOC teams.
Lorem ipsum dolor sit amet, consectetur adipiscing elit
Eliminate steps involving analysts’ investigation, standard escalation, and manual response following an alert. It acts on the data with automation and SOAR playbooks.

Lorem ipsum dolor sit amet, consectetur adipiscing elit

Lorem ipsum dolor sit amet, consectetur adipiscing elit
Keep track of your security posture and SOC team performance with comprehensive dynamic dashboards. Generate powerful reports for daily analysis or periodic updates to C-level executives.
Lorem ipsum dolor sit amet, consectetur adipiscing elit
Your on-demand partner for model development and advanced searches. It provides real-time insights, aids in fine-tuning, and suggests optimisations to accelerate your model-building process.

Lorem ipsum dolor sit amet, consectetur adipiscing elit
Fully flexible architecture capable of handling large volumes of data. Unlimited scalability to meet current and future organisational needs for growth.
MITRE ATT&CK® Coverage
MITRE ATT&CK® Coverage Header
Alignment with the MITRE ATT&CK framework enables detection of a wide range of behaviours, techniques and tactics while ensuring defences are optimised for the latest attack methods.

Data Residency
Data Residency Header
Compliant with data residency regulations in all countries
Continuous Fine-Tuning
Continuous Fine-Tuning Header

Virtual War Room
Virtual War Room Header
Siloed environment for incident response teams to collaborate in analysis, response, and mitigation of security threats and incidents.

Data Hygiene & Monitoring
Data Hygiene & Monitoring Header
System health checks provided by behavioural analytics of volume and trends of data flows.

Correlation & Alert Aggregation
Correlation & Alert Aggregation Header
Advanced correlation and aggregation of alerts for a meaningful visualisation of attack vectors and sophisticated predictive threat detection.

Ticket & Service Management
Ticket & Service Management Header
Built-in case management provides an overview of ticket lifecycles to organise and prioritise the most critical security incidents and track their resolution in real time.

Roster Management
Roster Management Header
Built-in roster management tool to handle resources allocation for efficient SOC operations.

Architected for high-powered performance and flexibility.
Platform
Web-based GUI
Lorem ipsum dolor sit amet, consectetur adipiscing elit Lorem ipsum dolor sit amet, consectetur adipiscing elit Lorem ipsum dolor sit amet, consectetur adipiscing elit

Algorithmic Framework
Deep Learning, Machine Learning.
Lorem ipsum dolor sit amet, consectetur adipiscing elit Lorem ipsum dolor
sit amet, consectetur adipiscing elit Lorem ipsum dolor sit amet,
consectetur adipiscing elit

User Authentication
User Authentication Title

Supported Environments
IT, OT, Blockchain.
Lorem ipsum dolor sit amet, consectetur adipiscing elit Lorem ipsum dolor
sit amet, consectetur adipiscing elit Lorem ipsum dolor sit amet,
consectetur adipiscing elit

Data Source Types
Data Source Types Title
Network Security, Endpoints, Cloud Services, Databases, User Activity,
Application Logs, Vulnerability Scanners, Physical Security Systems, Email
Security, and more.

Seamless Integrations
Plug and monitor
Log integration is made simple for rapid ingestion with a centralized and consolidated mechanism to fully manage and ensure adequate hygiene of your data sources. Support all standard PUSH, PULL, and file processing integration methods.

Data Analytics
Data Analytics Title

Cloud Native
Cloud Native Title
Deployment on cloud environment for scalability, flexibility, and ease of management.

Multitenancy Support
Multitenancy Support Title
Built to support multi-tenancy configuration seamlessly.

Secure by principle.
Proactive by design.

Compliance Frameworks
Flexible data architecture to manage data residencies and ensure compliance with data regulatory requirements, including ISO, PCI, GDPR, NIST, HIPAA, SOC2, and more.



System access is restricted based on a user’s role within an organization, ensuri
Accelerate your defence with Al-powered precision.
Lorem ipsum dolor sit amet, consectetur adipiscing elit Lorem ipsum dolor sit amet, consectetur adipiscing elit Lorem ipsum dolor sit amet, consectetur adipiscing elit
Remediation
Al-powered automation triggers predefined playbooks for rapid containment. Full integration capability with automation further improves your investigation and response.
Activity Monitoring & Reporting
Threat Center

Vendor-agnostic platform
Blacklight integrates with your existing security tools and data platforms without requiring you to centralise data or deploy new agents.

Cybersecurity’s Most Comprehensive AI Platform
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar leo.





